In an attempt to steal millions of credit card numbers, a ring of global hackers have infiltrated trusted Japanese websites, pushing a credit card fraud campaign, known as Morphixx. Thought to be one of the most cyber-secure countries in the world, Japanese users are now suffering at the hands of hackers who employ malicious clickbait ads to drain their bank accounts.
On June 23rd 2020, GeoEdge was first to detect the Global Morphixx attack in Europe, and since, attackers have remained lowkey until August 15, when a full-frontal attack was unleashed upon Japanese users. Because of the uptick in malicious attacks like Morphixx, hundreds of thousands of Japanese users a year fall victim to malicious clickbait scams that not onlywreak havoc on their personal finances, but cost the Japanese national economy millions.
Combining cyber capabilities and advanced social engineering techniques, credit card scams like Morphixx, are a nightmare scenario for any user, leading to debt and bankruptcy—while also serving as a steppingstone to identity theft. As the online fraud problem continues to sweep Japan, this attack is only the tip of the iceberg.
Once users slip Morphixx hackers their basic personal details and credit card numbers, the real malicious activity begins– underground. For most fraudsters, gaining credit card numbers is about more than simply making fraudulent purchases. As dark underground sales of data have transitioned into a criminal enterprise, the concerns over stolen data migrating to the dark web have become a terrifying reality. Upwards of 100,000 Japanese payment card numbers per year show up for sale on the dark web or “carding” websites, where stolen card data is bought and sold.
In order to trade this data on the dark web, Morphixx attackers first easily extracted users IP’s and prepared landing pages, designed with the logo, colors and language to match their Network provider. These personalized clickbait ads mimick users network provider, and allure users through advanced social engineering tactics. The attack then arrests the entire user experience and traps users in a bizarre gift lottery, making it impossible to escape and return to theiroriginal site. Regardless of the answers provided in the survey, users are directed to landing pages that reveal they’ve won a gift that requires their email and credit card information to redeem the prize. In the process, users are tricked into revealing their 16 digit payment card numbers in desperate attempts to get out of game loop.
Rather than young Japanese hooded hackers, the perpetrators behind The Morphixx campaign are not teen hackers with pseudo-magical powers but instead, an organized ring of cunning financially driven, highly organized cybercriminals.
Malware authors, like those behind this clickbait campaign, regularly and meticulously craft campaigns to target victims in particular countries- turning attacks on and off and bouncing from one location to the next. By constantly scanning all live campaigns — both the creative and landing pages in real time, GeoEdge’s security detection, managed to identify and precisely block only malicious impressions before users were exposed and scammed.
Let’s break down the attack path:
First, the attackers disguise their activity with a seemingly legitimate banner:

Next, an auto-redirect customized to the user’s internet network is automatically triggered with a deceptive offer to complete a survey, served on behalf of their network:
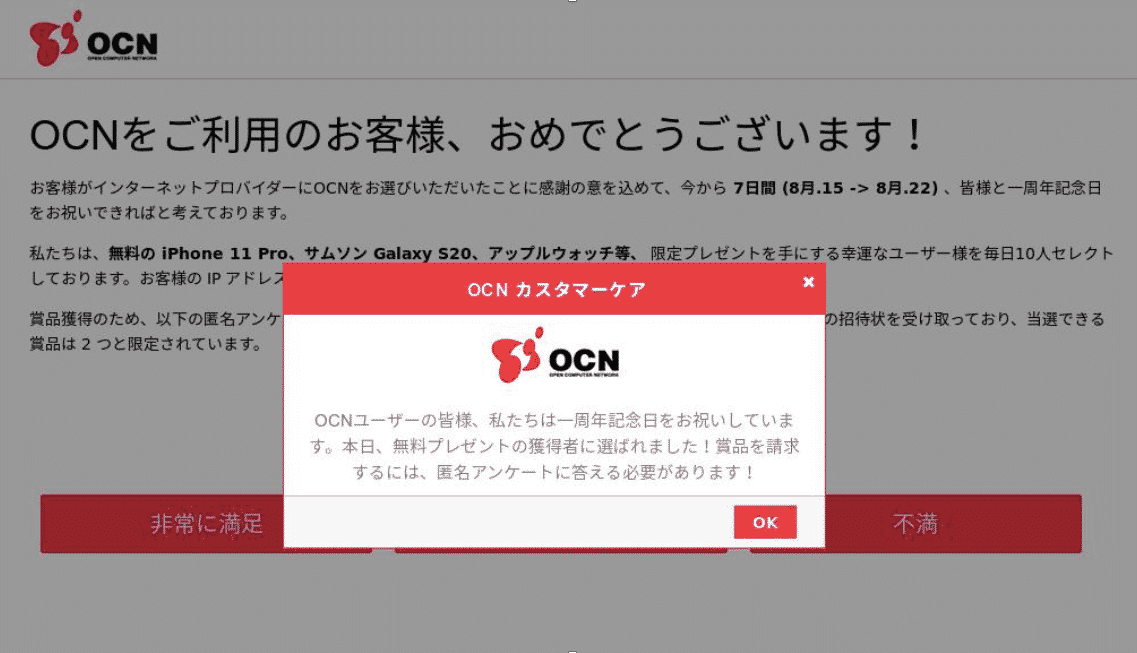
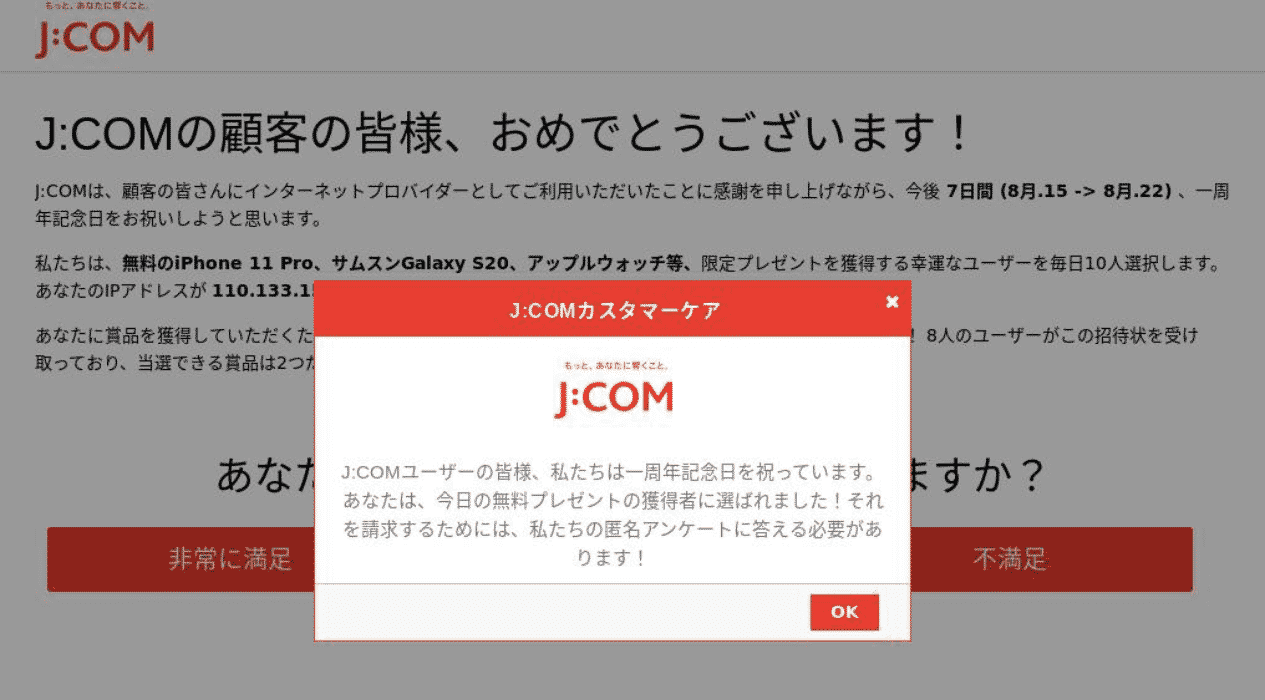

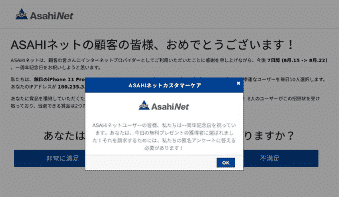
After completing the survey and regardless of the user’s answers, the malicious page automatically triggers a congratulatory message, announcing that users are entitled to a free mobile phone for which their email and credit card details are required.
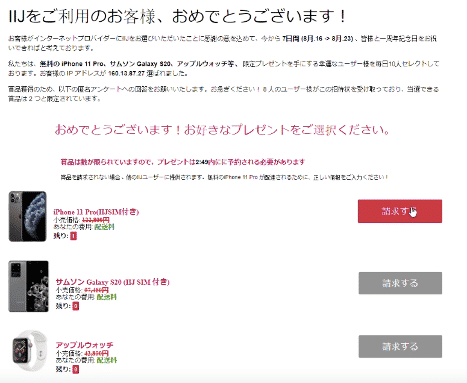
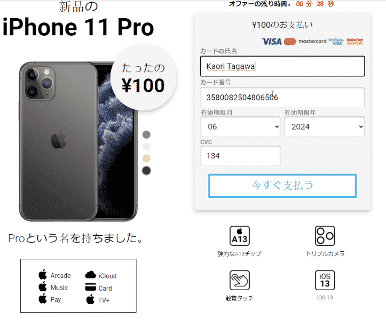
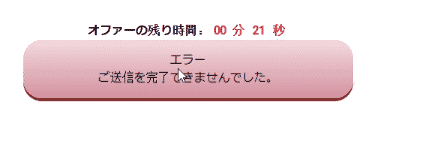
After typing in their name, and payment-card information, an error notice appears– so the user has no choice but to close the window without any notification that their credit card details have been recorded. While in fact the details have been captured– and are now ready to drain their bank funds.
The majority of malicious attacks targeting trusted websites occur outside normal working hours, during the night or over the weekend, as most companies don’t have IT staff working those shifts, and if they do, they are often short-handed. The attackers enabled the malicious Morphixx campaign creatives for less than 24 hours over the weekend, as it offered the best chance to slip-in without being noticed.
This type of clickbait scam is costing not only publishers strained relationships with their users but costing the national economy. The impact has been so severe, an investigation has been announced recently due to multiple complaints to Japan authorities about similar attacks.
The Morphixx campaign was proactively blocked using real-time detection, shielding users from the fake clickbait ad and game lottery entirely. Instead, the malicious creative was automatically replaced with a clean and safe ad, to ensure publisher’s ad revenue wasn’t harmed.
Users aren’t defenseless against cyberattacks as long as publishers embrace the right ad quality solution.
Traditional security solutions won’t cut it as scanning at multiple points along the supply chain is simply not enough– as cloaked ads reveal their true nature after the last scan. These malicious ad attacks are expressly designed to pass through a scan at the ad tag level, before the impression is rendered, and to show scanning technology a false result.
As the last line in defense against hackers, publishers can protect users from hackers attempting to steal their hard-earned money. When you need to keep bad ads off your site, knowledge is power. If you or other publishers have been affected by this attack, please contact GeoEdge for free immediate 30- day protection.
Contact us: [email protected]











